BLueEyes - Cybersecurity tickets management system


This desktop application aims to provide efficient way to handle many cybersecurity incident ticket. It will help security analyst team to better organize, prioritize, and collaborate on resolving these incidents quickly. The key features are:
With this app, analyst team can work together more effectively to triage, investigate, and resolve high volumes of cybersecurity incidents in timely manner.
Currently, security operations center face two main challenge when managing cybersecurity incidents:
Information Overload:
Too many tickets, unclear details, and poor prioritization hinder efficient analysis.
Collaboration Challenges:
Limited visibility into teammate activity, inefficient communication channels, and unclear escalation paths slow down collaboration.
These issues create bottlenecks and delays in responding to and resolving cybersecurity threats effectively. This new desktop application will solve these key problems.

Information Overload:

Collaboration Challenges:
As part of the empathy research process, I conducted user interviews with three participants who are cybersecurity analysts. The interviews aimed to gain insights into their experiences, challenges, and perspectives within the cybersecurity domain. The following questions were asked, and their responses are summarized below.


"I feel like I'm drowning in tickets! Half the time I don't even know what I'm looking at, and figuring out priorities takes forever."
Role: Tier 1 Security Analyst, 2 years experience.
Challenges: Struggles with high ticket volume, unclear ticket details, and difficulty prioritizing critical issues. Feels overloaded and stressed.
Needs: A system that prioritizes tickets automatically, provides clear and concise information, and offers filtering and search options for efficient ticket management.

"I feel like I'm working in a silo. I have no idea what my colleagues are doing, and getting help takes ages. We need a system that keeps us all on the same page."
Role: Security Analyst specializing in malware analysis, 5 years experience.
Challenges: Lacks visibility into team activity, struggles with inefficient communication channels, and finds escalation paths unclear. Feels isolated and frustrated.
Needs: A system with real-time updates, integrated chat or collaboration tools, and clear escalation procedures with role-based notifications.
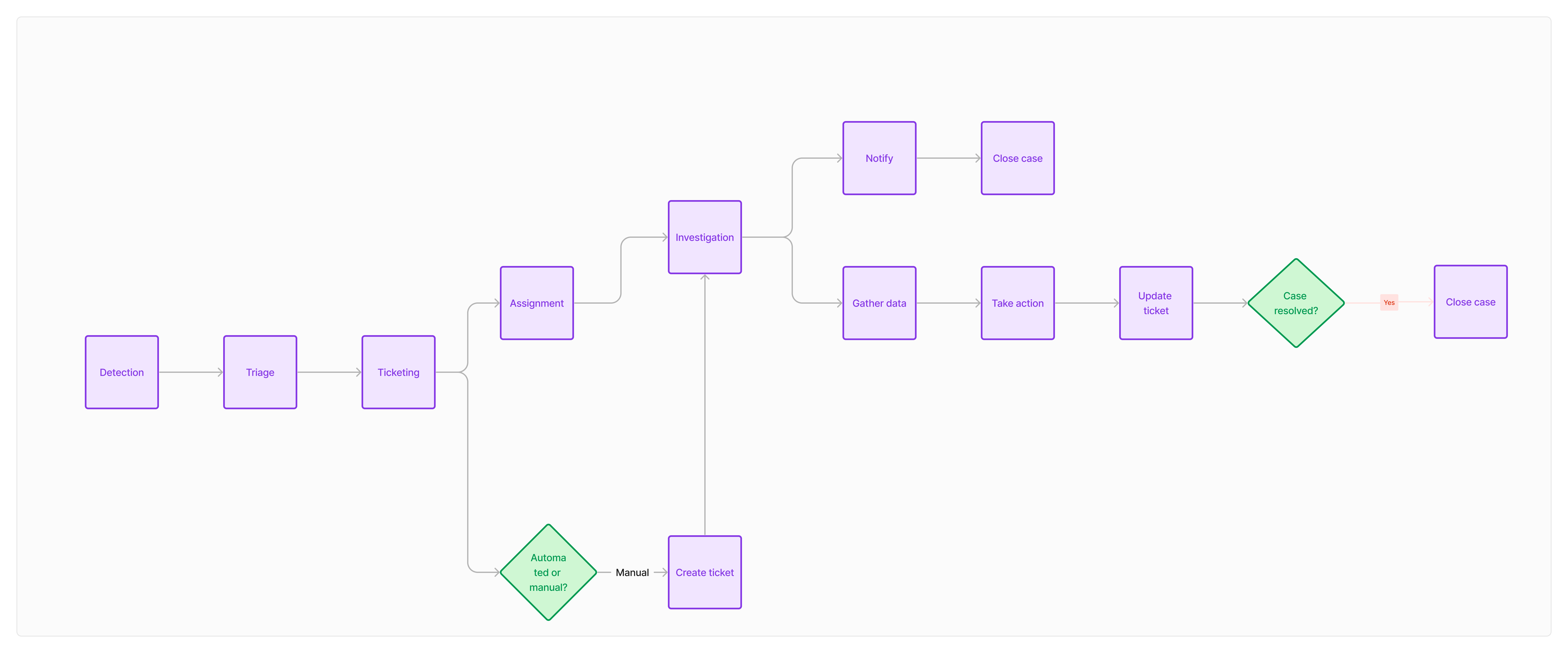
Streamlined User Flow: Incident to Analyst Notification